AI customer service systems are transforming how businesses interact with customers. But they also bring serious data security risks. Here’s what you need to know to protect sensitive information and maintain trust:
Key Security Measures:
- Data Protection: Encrypt sensitive data (e.g., AES-256) and secure cloud storage.
- Access Control: Use multi-factor authentication (MFA) and role-based access (RBAC).
- AI Model Security: Prevent attacks like data poisoning and model theft with regular testing and input validation.
- Compliance: Follow regulations like GDPR and CCPA, and conduct regular audits.
- Incident Response: Have a clear plan for detecting, containing, and recovering from breaches.
Quick Stats:
- 77% of businesses faced AI-related security breaches in the past year.
- Cloud breaches cost an average of $4.45M per incident in 2023.
- Role-based access can reduce security incidents by up to 75%.
Strengthening these areas ensures your AI systems remain secure and compliant while building customer confidence.
Data Collection and Storage Safety
Data Encryption Standards
AI customer service systems require top-tier encryption to protect sensitive information. AES-256 encryption is widely regarded as the standard for this purpose, offering strong protection. In fact, the U.S. Government uses AES to secure TOP SECRET data.
Here’s how encryption standards are applied:
| Security Layer | Requirements | Purpose |
|---|---|---|
| Data at Rest | AES-256 encryption | Protects stored customer information |
| Data in Transit | SSL/TLS protocols | Secures data during transmission |
| Key Management | Hardware Security Modules | Protects and manages encryption keys |
"AES 256 is a virtually impenetrable symmetric encryption algorithm that uses a 256-bit key to convert your plain text or data into a cipher." – Victor Kananda, Progress Blog
Strong encryption is the foundation for secure data storage, as described in the next section.
Cloud Storage Safety Steps
In 2023, 82% of breaches involved cloud-stored data, with average costs hitting $4.45 million per incident. To address these risks, organizations need to adopt cloud security protocols.
Some essential measures include:
- Access Management: Use multi-factor authentication (MFA) to block 99.9% of automated attacks and 96% of phishing attempts.
- Network Segmentation: Divide cloud storage into isolated sections to limit breaches and protect sensitive AI training data.
- Automated Monitoring: Use systems that log user activity and flag unusual behavior.
These steps work alongside encryption to secure data both at rest and during transmission.
Reducing Data Collection Risks
Collect only the data necessary for AI customer service operations. This reduces the risk of exposure and simplifies management.
| Data Type | Retention Period | Review Frequency |
|---|---|---|
| Customer ID | Duration of service | Quarterly |
| Transaction History | 2 years | Monthly |
| AI Training Data | Until model update | Bi-monthly |
Automating data retention ensures unnecessary information is securely deleted. Regular audits also help identify and remove outdated or redundant data, lowering the risk of exposure during security incidents.
Is Your AI Secure? Protecto‘s Data Guardrails for AI Explained
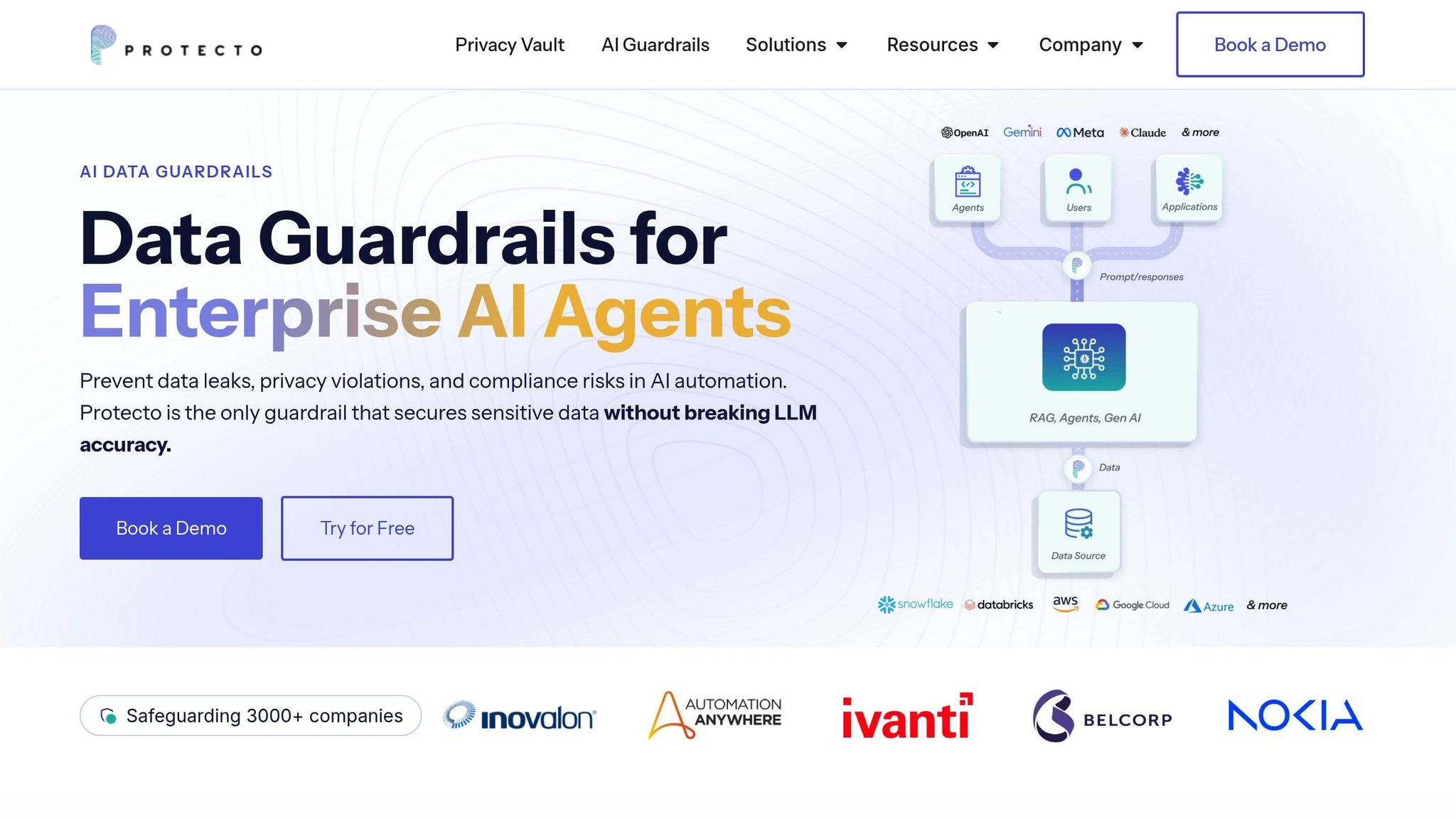
User Access and Login Security
Once data collection and storage are secured, managing system access becomes a critical step in ensuring overall security.
Setting Up Multi-Factor Authentication
Multi-factor authentication (MFA) adds an extra layer of protection by requiring users to verify their identity using multiple, independent factors. These factors typically fall into three categories: something the user knows, something the user has, or something the user is.
| Authentication Factor | Example | Security Level |
|---|---|---|
| Knowledge-based | Passwords, PINs | Basic |
| Possession-based | Smartphone OTP, Security Keys | High |
| Biometric | Fingerprints, Facial Recognition | Advanced |
Netflix’s ‘Service Code’ system is a great example of this in action. It generates one-time tokens for support interactions, simplifying caller identity verification.
"Ultimately, it is the company’s responsibility to keep their customers’ data safe and updating their authentication protocols over the phone is a really good way to start." – Rachel Tobac, CEO of SocialProof Security
Job-Based Access Limits
Role-based access control (RBAC) is a practical way to limit access and reduce risks in AI-driven customer service systems. According to IBM, implementing RBAC can cut security incidents by up to 75%. This is especially crucial as 65% of data breaches in 2023 were caused by internal actors.
Successful RBAC implementation relies on three key steps:
- Role Definition: Assign specific permissions to job functions.
- Access Constraints: Restrict access based on factors like time, location, or network.
- Regular Updates: Adjust permissions as roles evolve.
"Role-based access control (RBAC) assigns access based on job roles, ensuring employees only access information necessary for their responsibilities, reducing data breach risks."
Access Review and Tracking
Regular access reviews are essential to avoid incidents like the 2022 Cash App breach, which impacted 8 million customers. Consistent monitoring supports the encryption and cloud safety measures already in place.
| Review Component | Purpose |
|---|---|
| User Account Audit | Confirm active accounts |
| Permission Assessment | Check access rights |
| Privileged Access Review | Monitor high-level permissions |
Automated systems should track:
- Login attempts and unusual patterns
- Changes in permissions
- Data access history
- System modifications
Keeping detailed audit logs of access changes helps organizations maintain compliance and reinforce their security posture.
sbb-itb-a95661f
AI Model Protection
Securing AI models goes beyond safeguarding data storage and access. It requires a multi-layered approach to defend the models themselves.
Preventing AI Model Attacks
AI models face various risks. Below are key attack types, their potential effects, and strategies to counter them:
| Attack Type | Impact | Defense Measures |
|---|---|---|
| Data Poisoning | Corrupted training data | Input validation, data curation |
| Model Theft | Unauthorized access | Encryption, strict access controls |
| Adversarial Attacks | Manipulated outputs | Anomaly detection, input sanitization |
Layered defenses are crucial to mitigating these threats.
"Use adversarial example detection tools. Implement tools that actively monitor and identify adversarial inputs designed to mislead AI systems. By training a secondary model to detect anomalies in input data, you can safeguard systems against subtle evasion attacks".
Safe Model Development
Incorporating security measures during the development phase is essential to protect both algorithms and training data.
- Data Protection Protocols: Use differential privacy during training to prevent attackers from reverse-engineering sensitive data.
- Model Security: Restrict access with robust controls, secure model artifacts using hardware security modules, and rotate encryption keys regularly.
Model Testing and Updates
Ongoing testing and updates are key to addressing emerging threats. This includes continuous monitoring, regular vulnerability assessments, and automated anomaly detection.
"Leverage model explainability to detect anomalies. Use explainability techniques like SHAP or LIME to continuously validate AI decision-making processes. Sudden deviations in feature importance or decision paths could indicate tampering or exploitation attempts".
For industries like healthcare and finance, federated learning offers a way to train models across decentralized data sources without exposing sensitive information.
Meeting Legal Requirements
GDPR, CCPA, and Industry Rules
AI customer service systems must adhere to strict data protection laws like GDPR (effective May 25, 2018) and CCPA (effective January 1, 2020).
| Regulation | Key Requirements | Consumer Rights |
|---|---|---|
| GDPR | Limit data collection, require user consent, notify of breaches | Access personal data, request deletion, data portability |
| CCPA | Transparent data practices, opt-out options | Delete data, block data sales, ensure non-discrimination |
To comply, organizations should adopt privacy-focused frameworks. For example, Headspace uses proactive tools to simplify compliance.
"Our top priority is to have a solid privacy-by-design framework; tools like Checks that proactively provide needed information are extremely helpful to someone like me in a legal role so I don’t have to ask developers to provide it." – Kate F, Corporate Counsel at Headspace
Once these frameworks are in place, it’s crucial to ensure they’re actively enforced.
Security Compliance Checks
Alongside legal requirements, robust technical safeguards are essential for AI systems. The Global Privacy Assembly’s October 2023 resolution reaffirmed that existing data protection laws apply to AI services, even as new AI-specific rules are developed.
To stay compliant:
- Classify AI applications by their risk level and sensitivity.
- Use AI tools to enforce security protocols.
- Conduct Data Protection Impact Assessments (DPIAs) for high-risk projects.
Thorough documentation is equally important to demonstrate adherence to these standards.
Record Keeping Requirements
Comprehensive documentation is vital for meeting data protection regulations. Key records to maintain include:
| Document Type | Purpose | Update Frequency |
|---|---|---|
| Risk Register | Track risks and mitigation actions | Quarterly |
| DPIA Records | Log impact assessments and decisions | Per project |
| DPO Decisions | Record recommendations from the Data Protection Officer | As needed |
For example, Spotify, a Mailchimp client, documented its Email Verification API in March 2023. This effort reduced bounce rates from 12.3% to 2.1% in just 60 days, improved email deliverability by 34%, and generated $2.3M in revenue – all while staying GDPR-compliant.
To maintain compliance over time:
- Implement strict data retention policies.
- Document all data processing activities.
- Keep detailed consent records.
- Maintain security audit logs.
- Store records of data subject requests.
"We take data privacy seriously at Kustomer." – Kustomer
This focus on detailed documentation not only satisfies regulatory demands but also strengthens trust with customers and stakeholders.
Security Breach Response
AI Security Emergency Plan
Having a solid incident response plan is crucial for safeguarding AI customer service systems. This plan should integrate Model Risk Management (MRM) practices with standard incident response protocols to ensure a comprehensive approach.
| Plan Component | Key Actions | Monitoring Requirements |
|---|---|---|
| Prevention | Document AI system assets; implement security measures | Ongoing system monitoring |
| Detection | Use AI for threat detection; monitor system behavior | Real-time anomaly detection |
| Response | Activate the incident response team; isolate affected systems | Log and track activities |
| Recovery | Restore from secure backups; strengthen security measures | Monitor system performance |
Here’s a closer look at the immediate steps to take when a breach occurs.
Data Breach Response Steps
High-profile breaches highlight how critical a fast response is. For instance, when T-Mobile experienced a breach in November 2022 that exposed 37 million customer records through an AI-powered API, their quick action helped limit the fallout.
Key response actions include:
- Immediate Containment
Quickly isolate compromised systems to stop further damage. For example, Yum! Brands dealt with a ransomware attack in January 2023 by immediately shutting down affected systems, which temporarily closed nearly 300 UK locations. - Investigation and Documentation
Conduct a detailed forensic investigation to uncover how the breach happened, assess the extent of compromised data, evaluate the impact on AI models, and determine if regulatory notifications are required. - Stakeholder Communication
Transparent communication is vital. When TaskRabbit faced a breach in April 2018 affecting 3.75 million records, they prioritized clear updates to both users and regulators.
These steps build on earlier prevention strategies to ensure a well-rounded security approach. Once containment and communication are handled, efforts shift toward system recovery.
System Recovery Steps
Recovering AI systems after a breach means restoring operations while strengthening security to prevent future incidents. The recovery process includes:
| Recovery Phase | Actions | Validation Steps |
|---|---|---|
| Initial Assessment | Assess system damage; identify affected components | Conduct security scans |
| Data Restoration | Restore from clean backups; verify data integrity | Perform data consistency checks |
| System Hardening | Strengthen security controls; fix vulnerabilities | Test through penetration testing |
| Operational Return | Gradually bring systems back online; monitor performance | Benchmark system performance |
To enhance recovery efforts, consider using an AI Incident Response Toolkit, conducting post-incident reviews, and continuously updating your response strategies.
Conclusion: Maintaining AI Data Security
Key Security Measures
Securing an AI system requires multiple layers of defense. AI-related security incidents have grown by an astonishing 690% between 2017 and 2023.
Here’s a breakdown of the essential security layers:
| Security Layer | What It Involves | What to Monitor |
|---|---|---|
| Data Protection | Encryption, data masking, sanitization | Real-time anomaly detection |
| Access Control | Zero-trust architecture, MFA | Continuous authentication |
| Model Security | Containerization, gradient masking | Performance monitoring |
| Compliance | GDPR framework integration | Regular audits |
With 70% of organizations now using managed AI services, these steps are critical. They not only protect sensitive data but also help build trust with customers.
Linking Security to Customer Confidence
Concerns about AI and data privacy are widespread – 57% of global consumers fear that generative AI could compromise their personal data, and 43% express distrust in AI-driven interactions.
To address these concerns, companies need to focus on:
- Clear Communication: Be upfront about how AI systems protect customer data. Transparency goes a long way in easing fears.
- Active Protection: Use AI threat intelligence tools and monitor systems continuously to stay ahead of potential risks.
- Empowering Customers: Offer tools that allow users to manage and control their personal data directly.
Experts stress the importance of staying agile in the face of evolving threats. Regularly updating security measures and conducting reviews are key to staying ahead of vulnerabilities. As AI technology progresses, maintaining transparency and adapting security practices will remain essential.


Leave a Reply